Kerberos Authentication
Kerberos authentication protects user credentials from hackers. To mitigate this problem it is recommended that the users use lengthy passwords.

Linked Server Double Hop Issues With Sql Server When Sql Server Cannot Use Kerberos It Defaults To Ntlm Which Is A Challenge Respo Sql Server Sql Name Server
The user cannot authenticate because the ticket that Kerberos builds to represent the user is not large enough to contain all of the users group memberships.

Kerberos authentication. Many people consider configuring Kerberos authentication and making it work as a daunting task. However it does not prevent a passive attacker from sniffing the clients encrypted timestamp message to the KDC. Thus Kerberos pre-authentication can prevent the active attacker.
The idea behind Kerberos is to authenticate users while preventing passwords from being sent over the internet. Kerberos is a computer network security protocol that authenticates service requests between two or more trusted hosts across an untrusted network like the internet. Kerberos replaced NT LAN Manager NTLM as the default authentication for Windows OS as a much faster and safer alternative.
Kerberos authentication provides a highly secure method to authenticate client and server entities security principals on a network. In our world Kerberos is the computer network authentication protocol initially developed in the 1980s by Massachusetts Institute of Technology MIT computer scientists. Typically a network application needs to know some attributes such as the name about the party sending it messages.
One of the reasons for this is different configuration elements involved in the process. Microsoft introduced their version of Kerberos in Windows2000. Provided is essential to validating the integration of Kerberos into an application.
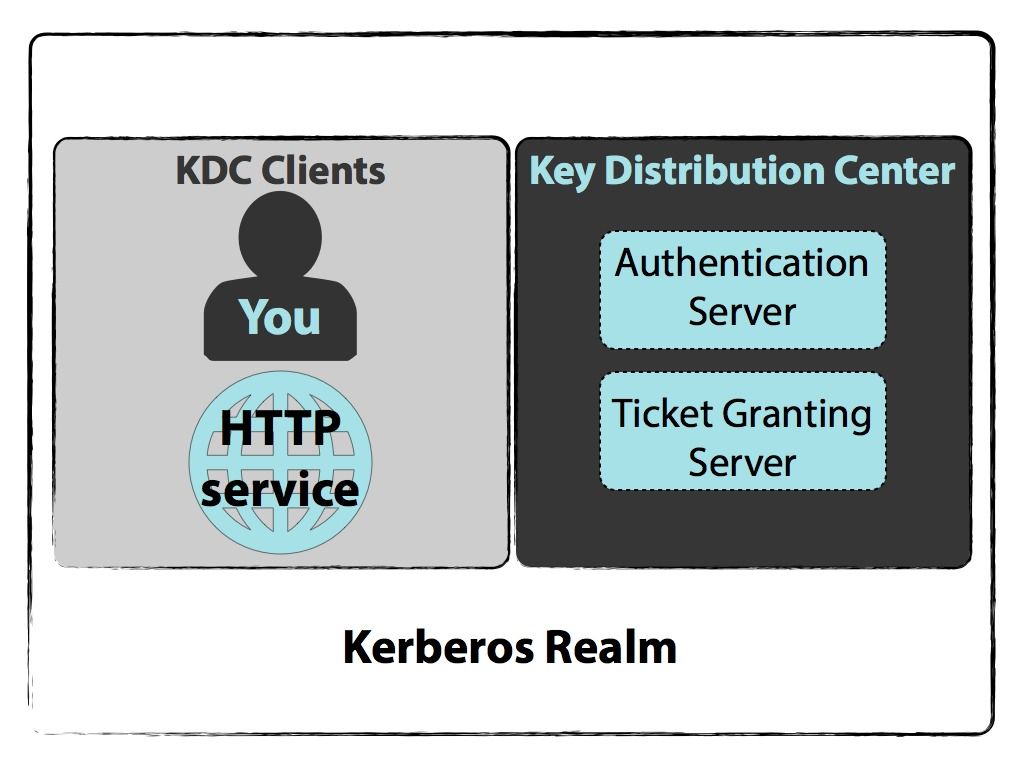
Kerberos runs as a third-party trusted server known as the Key Distribution Center KDC. Kerberos is an authentication protocol that can provide secure network login or SSO for various services over a non-secure network. Kerberos is an authentication protocol for clientserver applications.
Kerberos works with the concept of tickets which are encrypted and can help reduce the amount of times passwords need to be sent over the network. If the attacker can sniff that full packet he can brute force it offline. Each user and service on the network is a principal.
As part of the Authentication Service Exchange Windows builds a token to represent the user for purposes of authorization. Kerberos provides a centralized authentication server whose function is to authenticate users to servers and servers to users. Negotiate is a provider or container which supports Kerberos protocol and it also.
In order to setup Kerberos for the site make sure Negotiate is at the top of the list in providers section that you can see when you select windows authentication. Authentication Authentication is the process of verifying to a sufficient degree of confidence claims about a party or message. In Kerberos Authentication server and database is used for client authentication.
It might also use NTLM which is also a provider in windows authentication. IT administrators can enable auditing of Kerberos authentication which allows recording of events created during this process. Kerberos authentication is currently the default authorization technology used by Microsoft Windows and implementations of Kerberos exist in Apple OS FreeBSD UNIX and Linux.
One such important configuration is setting the appropriate SPN. To use Kerberos authentication with SQL Server a Service Principal Name SPN must be registered with Active Directory which plays the role of the Key Distribution Center in a Windows domain. This protocol keeps passwords away from insecure networks at all times even during user verification.
Read on to learn what Kerberos authentication is and how it protects both end-users and systems. 3 Enabling windows authentication doesnt mean Kerberos protocol will be used. It uses secret-key cryptography and a trusted third party for authenticating client.

Configuring Kerberos Authentication In Different Browsers Browser Internet Options Web Server

Flink Configuring Kerberos Authentication Huawei Enterprise Support Community Unified Communications Public Security Ip Telephony

A Brief Tutorial About Kerberos And It S Integration With Cloudera Hadoop Cluster Installation Custer Security

How Do I Use Ntlm Or Kerberos Authentication To Access A Cifs Share In 2021 Trust In Relationships Messages Access
Explain Like I M 5 Kerberos Lynn Root Explained Words Cryptography

Kerbrute A Tool To Perform Kerberos Pre Auth Bruteforcing Cyber Security 20 Years Old Linux

Optimizing Ntlm Authentication Flow In Multi Domain Environments Cyber Security Optimization Computer Server

Part2 Step By Step Guide For Configuring Kerberos Authentication In Sharepoint 2013 2016 Sharepoint Microsoft Dynamics Step Guide

Authentication Fails When A Windows Client Accesses A Cifs Share Because The Kerberos Authentication Ticket Is Cached In 2021 Windows Client Fails Clients

Kerberos Architecture Computer Help Windows Server Microsoft

Sap Hana Authentication Methods For Verification Of User Identity Username Password Kerberos Saml Sap Logon Tickets And Assertion Sap Hana Markup Language

Authentication Fails When A Windows Client Accesses A Cifs Share Because The Kerberos Authentication Ticket Is Cached In 2021 Windows Client Clients Fails

Request Based Versus Session Based Kerberos Authentication Or The Authpersistnonntlm Parameter Request Sharepoint Base

Register A Spn For Sql Server Authentication With Kerberos Sql Server Microsoft Sql Server Sql

Cracking Kerberos Tgs Tickets Using Kerberoast Exploiting Kerberos To Compromise The Active Directory Domain Active Directory Innovation Technology Domain

Mongodb Authentication With Kerberos Regular Expression Data Storage Reading

Kerberos Architecture Computer Help Windows Server Microsoft

Apache Flink Provides First Class Support For Authentication Of Kerberos Only While Providing Effortless Requirements To All C Apache Security Activity Monitor

0 Response to "Kerberos Authentication"
Post a Comment